Organizations that offer applications via Software-as-a-Service (SaaS) to their business customers often have a need for Customer Identity and Access Management (CIAM) capability. In this article, multi-tenancy means that our business-to-business (B2B) SaaS application can support multiple tenants, where each tenant is simply a grouping of users. Therefore, each business customer organization is a distinct tenant that needs access to a single instance of the B2B SaaS software application that runs on a server somewhere.
In this article, we discuss B2B SaaS applications that are multi-tenant, not single-tenant! Note that we don’t discuss single-tenant B2B SaaS applications, as the majority of B2B SaaS apps are multi-tenant in nature.
In general, customers can be divided into three main categories:
- Individual consumers
- Business/enterprise customers
- In a more complex scenario, a business customer can, in turn, be a channel partner such as a distributor or reseller that would then manage and control access of their own customers to access the multi-tenant B2B SaaS application.
- Citizens
The following diagram shows the three main subcategories of Customer Identity and Access Management (CIAM):
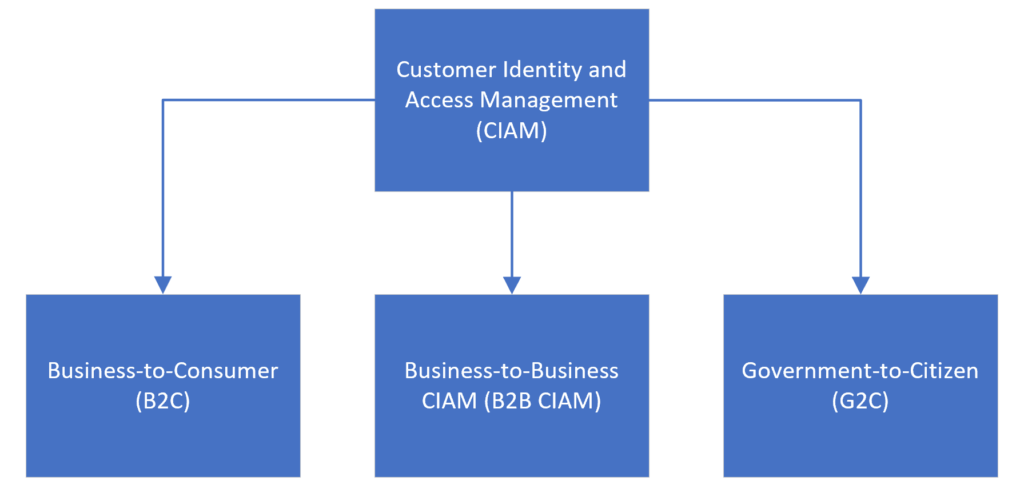
Consumers are individual customers and there is usually no hierarchy or relationship between them. When many talk about business-to-consumer (B2C), they usually mean that the customer is a consumer. You can have many millions of consumer user accounts, and each consumer user account is independent of another. Also, there may not need to be a concept of permissions because every consumer can perform the same functionality as any other consumer.
In contrast, business customers are organizations (e.g., legal entities) that will be accessing your multi-tenant SaaS application. Although B2C can also encapsulate business customers, the more frequently used term is B2B CIAM, which makes it clear that the customers are businesses, not individual consumers.
Arguably, B2B CIAM is a lot more complex to implement than simply enabling individual consumers to access your SaaS application. In fact, unlike B2C, if you offer a SaaS application to your business customers, then most likely it will be a multi-tenant SaaS application, where each tenant is an organization. In addition, unlike consumers, there is usually a hierarchy within each business customer, such that an administrator within that organization can add or remove other end users from their company to access your multi-tenant SaaS application. Therefore, if you are offering a SaaS product to individual consumers, you rarely have to think about multi-tenancy, because you don’t have a need to group users together.
There are many popular CIAM products on the market such as Microsoft Entra External ID, Auth0 by Okta, Azure Active Directory B2C (AAD B2C), and many others. All these products offer CIAM capabilities, both for B2C as well as for B2B CIAM.
The following diagram illustrates both the legacy and modern approaches to CIAM:
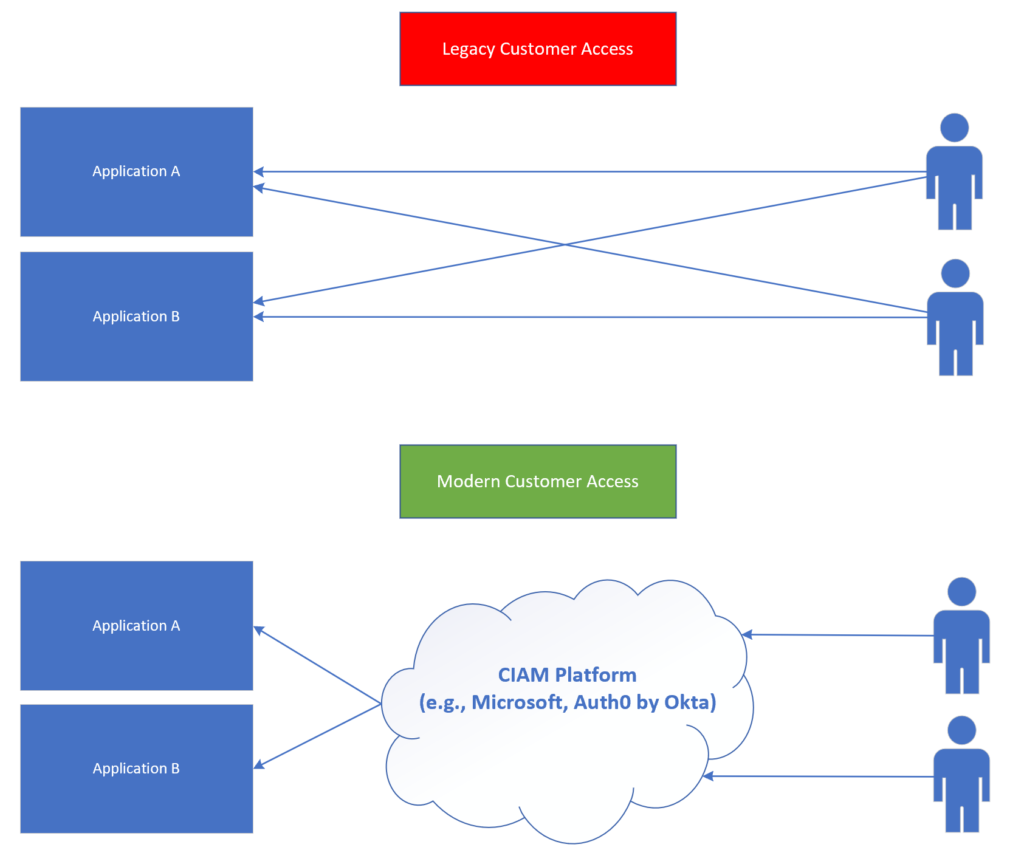
As you can see from the diagram above, the main difference between the legacy customer access approach versus modern customer access is that in the modern approach, an end user doesn’t directly authenticate to the customer applications, but rather they authenticate to the customer applications through the CIAM platform. Obviously, there are many benefits to this approach, such as:
- Centralized User Account Directory
- All end user accounts from across your customer tenants are stored in a centralized directory service.
- Each user account has user profile information, which is normalized, regardless of which identity provider (IdP) the end user was using to authenticate. Since each IdP can have its own terminology for user account attributes, the SaaS application doesn’t need to concern itself with this complexity, as it relies on core attributes present in the centralized user account profiles in CIAM.
- Even if the user account requires a password to be managed, or a passwordless option is needed, this is centralized. Therefore, an end user can easily change their password and/or change passwordless credentials, without the need to do this for each SaaS application individually in your application portfolio.
- Enterprise Federation
- End users benefit from Single Sign-On (SSO) capabilities and can authenticate and perform multi-factor authentication (MFA) with their corporate identity provider (IdP), such as Entra ID, Google Workspace, Okta, etc. This will empower business customers to Bring Your Own Identity (BYOI), which would simplify user onboarding, access management, and lifecycle management.
- With federated SSO authentication, a business customer employee can authenticate once, and receive access to all their B2B SaaS applications.
- Authentication using Home Realm Discovery (HRD)
- In a multi-tenant B2B SaaS application, it is important to customize the HRD process, so that the end user can either choose or be automatically redirected to their organization’s authentication system (e.g., using email domains to route to the specific upstream IdP).
- Delegated Administration
- Managing end user accounts is a big burden on the B2B SaaS provider and help desk personnel. As a result, most CIAM platform vendors offer self-service delegated administration capabilities, usually via user administration management APIs, which enables customer administrators to, in turn, manage their own staff, in a hierarchical manner.
- Authorization
- In addition to offering authentication services, CIAM vendors offer the ability to externalize authorization capabilities, usually via groups, role-based access control (RBAC), or attribute-based access control (ABAC). Authorization can be coarse-grained or fine-grained. The goal is to enable business customers to autonomously manage their own user/group access rights. In addition, you can use centralized authorization policies to control which business customers have access to which B2B SaaS applications in your multi-app portfolio.
To summarize, if you are designing and developing multi-tenant B2B SaaS applications, you should be leveraging a CIAM platform vendor that can decouple your B2B SaaS applications from upstream identity providers. Although implementing traditional B2C capabilities is not trivial, B2B CIAM is significantly more complex, and requires careful consideration of the multi-tenant architecture of your SaaS application, with the goal of offering as much self-service capability to your business customers as possible. Due to its very nature, B2B CIAM requires customization and adaptation to the many tenants/customers that it will service.
By leveraging a CIAM platform that supports B2B CIAM capabilities, you can reduce the workload on your own staff (both sales and support) and focus on business value and functionality that drives revenue for your B2B SaaS solutions.